Is HIVE Ransomware Dead?
TLDR: The FBI's recently announced a successful takeover of Hive servers and the release of ransomware encryption keys. While the disruption of operations and release of keys is certainly a positive, no arrests were made, the software is not eradicated and the ability to rotate keys is trivial. With decentralized operations across the globe, we expect that the individuals associated with the HIVE gang to simply move operations to new servers in a new location and regenerate keys and start again. So is HIVE dead? - In name, perhaps. In practice? Unlikely.
On January 26th, 2023, The United States Justice Department took action against the Hive ransomware gang that had successfully executed 1,500 ransomware attacks in 80 countries. The FBI announced they were able to get into Hive's networks, capture the active encryption keys, and have made them available to victims. The FBI has helped over 300 victims in this bust and, consequently, seized control of Hive's servers and websites, making it harder for them to continue their attacks. This effort was made in cooperation with law enforcement in Germany and the Netherlands.
What does it mean when they say “capture encryption keys”? To understand this, let us quickly break down how ransomware encryption works at a high level.
-
After infiltrating the environment and identifying target files, threat actors apply symmetric encryption to lock individual files. Why symmetric encryption? It is FAST, efficient, and uses the same key to encrypt and decrypt.
-
Once files are encrypted, asymmetric encryption is applied to “lock” the file keys themselves using the public/private key pair. The victim needs the private key to decrypt, making it nearly impossible to decrypt without paying. This asymmetric process is utilized in this last step because while extremely sound, it is slow and resource-heavy. It would likely be identified by a detection system before it could complete.
-
Once the ransom is paid, the victim organization receives the decryptor with that private key embedded to “unlock” the file's symmetric keys and, in turn, be able to execute the symmetric decryption to unlock individual files with the individual file keys.
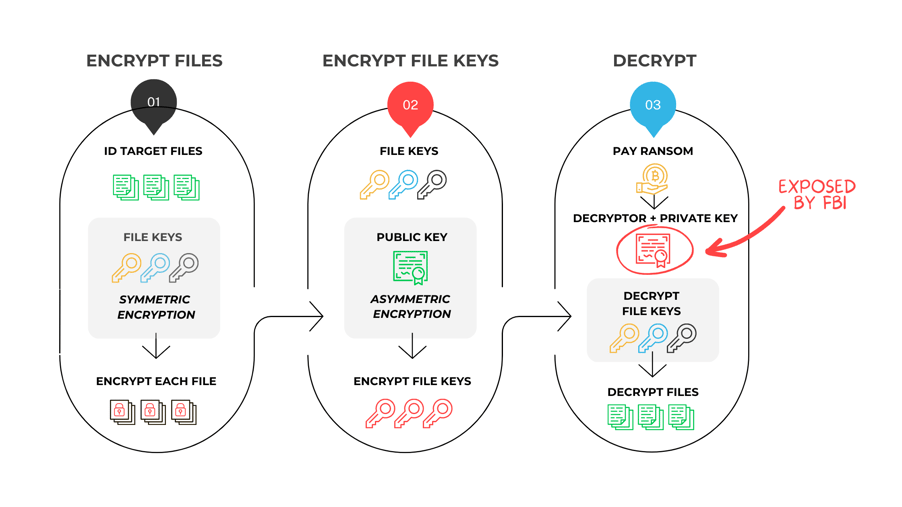
The good news: By exposing the private keys, the FBI provided a way for victims to decrypt their data without supporting the ransomware business model. Several HIVE decryptors have been made available by trustworthy organizations, saving upwards of $100 million. Additionally, by disrupting the communications and intercepting servers, the Hive gang is, at a minimum, forced “underground” for some time.
The bad news: This doesn’t mean that Hive is gone forever.
-
Software is Not Eliminated: Ransomware software itself is persistent, with defunct code often resurfacing in new or hybrid ransomware. The proliferation of the Ransomware-as-a-Service (RaaS) model has facilitated the widespread distribution of software, allowing for continued use of their SDKs and the further evolution by their creators
What is RaaS? - Ransomware as a service (RaaS) is a model where criminals create and distribute malicious software and other services to other operatives, who use it to launch their own attacks. RaaS lowers the barrier to entry for cybercriminals and has led to a proliferation of new strains of ransomware. -
Key Rotation: Ransomware gangs regularly rotate their encryption keys. In reality, all they need to do is create new public-private key pairs, and they can begin again.
-
No Arrests: There were no physical arrests in this case, and the criminals behind HIVE are still “at large.” It remains unclear whether they will resurface under their original moniker, as was the case with REVIL, or take the time to reorganize and reestablish themselves under new identities, similar to Conti, who has spun off and formed Blackcat, Quantum, and most recently, HIVE. Given these developments, it is reasonable to expect that HIVE may reemerge in some capacity in the near future.
-
Decentralized Operations Ransomware groups operate with a decentralized structure in which various members undertake different aspects of the attack. Hive has enjoyed considerable financial success in recent years. They possess the capacity to establish fresh servers in any location, upgrade their software, and resume their nefarious operations.
In conclusion, is Hive disrupted? - Yes. Do recent victims now have a path to recover without paying the ransom? Yes. But is Hive gone forever? Unfortunately, not likely.
A New Decryption Capability:
The problem remains: Ransomware continues to get passed cyber-security systems, and when they do, they find or create gaps in backups, snapshots, and other data resilience systems. It will take a combination of technology, law enforcement, and personnel to fortify organizations from ransomware.
In the case of Hive, decryption is possible due to law enforcement. But, with spinoffs, this could be short-lived. Nubeva introduced a new capability that allows organizations to add decryption to any data resilience strategy, with a 99% decryption success rate against any ransomware software. The capability enables organizations to decrypt without key exposure and without paying the ransom.
Join us on our upcoming technical brown bag to learn more: Register Here
Subscribe to our newsletter
Related Blogs
Healthcare providers are no strangers to ransomware attacks, as cyber attackers often...
The White House has released an update on the National Cybersecurity Strategy,...
Ransomware has become a catastrophic disaster to business continuity and operations....

