Make Your Wireshark See All
Wireshark is a core application in any security professional or systems administrators toolbox. As the world’s leading network traffic analyzer, Wireshark is heavily relied upon to analyze network traffic in real-time for troubleshooting, event inspection and forensic analysis on flagged anomalies and threat detection.
Whether in the cloud, where TLS standards are managed and enforced by your cloud provider, or on-prem, organizations are moving to higher levels of end-to-end SSL/TLS encryption for improved compliance and security - TLS 1.3 and Perfect Forward Secrecy (PFS) being the protocol in place today.
As with any investigation, the evidence is key to reach the solution - the more facts and evidence you have, the better - the more details and clues, the faster you can come to the final conclusion for action. The ultimate goal for analysis is to find the problem, gather the evidence and solve/respond to the incident as quickly as possible, with the fewest possible “casualties.” You wouldn’t turn down evidence in a case if it was easily available to you.

Let's break down a forensic investigation scenario with Wireshark:
A network or security analyst is routinely assigned a ticket for deeper inspection or is working to respond to an event. Using the available data (perhaps via flow/cloud logs or JA3/data etc.) it is identified that this specific instance requires further packet investigation. A common scenario is to use TCPdump to grab the packet output and load that data into Wireshark. When opening the packet, the data is fully encrypted due to the implementation of Elliptic-curve iffie-Hellman and perfect forward secrecy. Inspecting this traffic could be compared to dissecting a document with redacted content. While you may be able to make some inferences and triangulate causation, wouldn’t it just be easier if you could decrypt the traffic to really dig into what is going on?
If you’ve experienced this in the past, you know it is no doubt a challenge to get around. If you haven’t, you likely will soon with the mass adoption of the new TLS protocols. These protocols have broken traditional methods for decryption. Out-of-band decryption is impossible and with the complexity of new application architectures and growth of elastic east-west traffic, using man-in-the-middle decryption creates operational inefficiencies on your teams and network.
The “Key” Problem: At its most basic, the introduction of PFS and Diffie-Hellman - when clients talk to servers and go through the encryption handshake, they create a symmetric key that is only relevant to that individual session - also called a final secret, bulk encryption key or ephemeral key. In the legacy world, you could regenerate the keys, using certificates in the packet themselves to regenerate the keys and then decrypt the session. In the new world, however, you can’t do this. If you cannot get the symmetric keys, you can’t decrypt, which has essentially broken all legacy out-of-band decryption options. Learn More
Decrypted Visibility with Wireshark: There is a new way! You can now maintain end-to-end encryption and the ability to decrypt modern SSL/TLS traffic out-of-band!
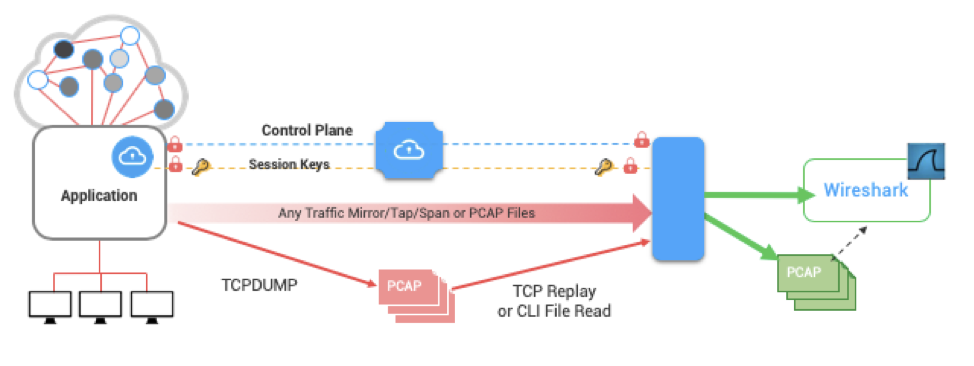
Symmetric Key Intercept allows organizations to get their hands on their symmetric keys! Remember, symmetric keys are not the same as final encryption keys of the past! They are per-session only, and must be paired with the traffic to mean anything. This new architecture maintains separation of the keys and the copy of the traffic - and all data is encrypted in-motion - maintaining a low-risk profile.
Enforce end-to-end encryption, with the highest cipher levels, while still allowing security analysts and engineers to do their job - quickly with little to no disruption, at scale, with your tool of choice! With this solution, you are able to decrypt packets on your wireshark tool allowing your wireshark instance (or really any tool of your choice) to complete your investigations, faster. Read more as we break down how you can gain decrypted visibility for Wireshark with Symmetric Key Intercept. Check out this Cloud Formation Template to set it up and test it yourself!

