Malware Hidden in TLS Encrypted Traffic Doubles.
How Are Your Security Teams Keeping Up with the Malware Hiding in TLS Encrypted Traffic?
A recent study by Sophos shows that 23% of the Malware detected in 2020 was encrypted with the Transport Layer Security (TLS) protocol. However, in the first three months of 2021, the figure had grown to nearly 46%. With the adoption of TLS 1.3 and TLS 1.2 with PFS, security systems are struggling to keep up, allowing malicious traffic to slip through the cracks. As an additional complication, not only does malware “land” via encryption, it is well known that malware regularly hides its executions (lateral movement, command-and-control, data exfiltration, etc.) using TLS encryption inside normal traffic patterns. In short, it's getting harder and harder to detect and protect against malware in the face of modern encryption.
Unfortunately, traditional enterprise-class techniques for inspecting encrypted traffic are failing as well.
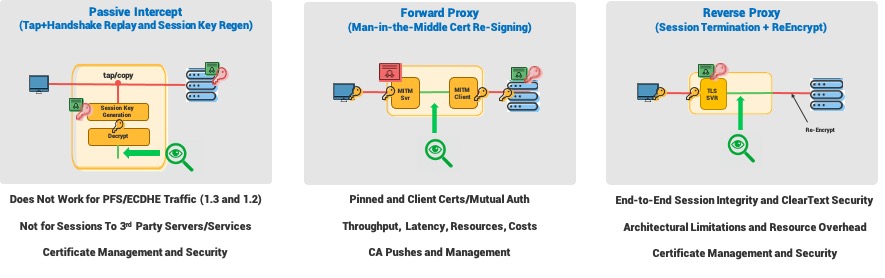
Passive inspection techniques do not work with perfect forward secrecy-based encryption- plain and simple - essentially obsoleting any technologies or systems that use this method without an alternative decryption method.
That leaves inline solutions that employ man-in-the-middle or SSL termination methods, such as nextgen firewalls, secure web gateways, intrusion prevention systems, and more. Both of these methods have growing issues with newer TLS protocols, ever-changing application architectures, and sheer network scale. These issues include limited functionality, constant and complex operations, and administration, performance considerations including latency and throughput bottlenecks. Not to forget, the exploding costs (CAPEX and OPEX). These challenges limit product viability and ultimately increase risk by allowing malware to run undetected for long periods of time before it is even detected. In the 2020 M-Trends report, the global median dwell time, defined as the duration between the start of a cyber intrusion and it being identified, was 56 days. With security systems failing due to encryption, safe to hypothesize that this will only grow.
The Answer: Nubeva SKI - A New Option for the New Era of TLS:
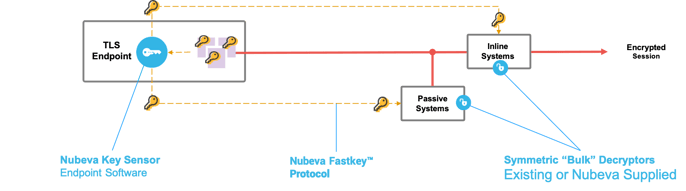
A New Option for the New Era of TLS:
Nubeva offers solution providers an option to enhance and/or augment their already mature and trusted systems. Nubeva's TLS decryption technology (Session Key Intercept) is already breathing back to life full network inspection for our customers with our OEM offering, providing a way to fill the gap without reinventing the wheel. Nubeva is working with both leading solution providers and up-and-comers looking to capture market share and competitive differentiation.
SKI enables full packet inspection for commercial, open-source, and homegrown tools.
With Malware sneaking by in encrypted traffic, security systems failing to offer full packet inspection is not an option for the modern era is not an option for enterprises.
Learn how Nubeva can partner with your technology by watching our recent Technical Brownbag or contact us to learn more.

