It's About The Keys: Using SKI to See into All Traffic
Read Time: 8 minutes
TL;DR
Our innovation, Symmetric Key Intercept, enables you to discover and use final, symmetric session keys to decrypt and inspect traffic at line-rate speed. This solution replaces outdated, man-in-the-middle systems that slow your systems and cost money to maintain and reintroduces the out-of-band option. Symmetric Key Intercept is designed for modern TLS and enables deep packet inspection across active/inline, passive/out-of-band and new, greenfield compute environments.
In our May Technical Brown Bag, Steve Perkins, head of product at Nubeva, delivered an online whiteboard architecture session and walked through our new Symmetric Key Intercept technology. The solution is simple. It allows users to get full visibility into packet payloads in public cloud environments and in their data centers. If you weren’t able to join us, you can view the on-demand Brown Bag session here.
The recorded presentation explains Symmetric Key Intercept, the problems it solves and how organizations can use it today to obtain more network traffic visibility.
Here’s a recap of the discussion:
What’s the Challenge?
 Encryption started more than 20 years ago with the creation of SSL, which transitioned to TLS. Today, TLS 1.2 with perfect forward secrecy (PFS) and TLS 1.3 are the new standards resulting in more than 80% of all network traffic being encrypted. And while encryption standards have evolved rapidly in recent years, the methods used to see into this traffic have not kept pace. It all nets out to the fact that new encryption provides better privacy and protection for data in motion while blinding legacy decryption and the subsequent that rely on decrypted packet visibility.
Encryption started more than 20 years ago with the creation of SSL, which transitioned to TLS. Today, TLS 1.2 with perfect forward secrecy (PFS) and TLS 1.3 are the new standards resulting in more than 80% of all network traffic being encrypted. And while encryption standards have evolved rapidly in recent years, the methods used to see into this traffic have not kept pace. It all nets out to the fact that new encryption provides better privacy and protection for data in motion while blinding legacy decryption and the subsequent that rely on decrypted packet visibility.
The core challenge is that decryption requires three things, one of which is very difficult to get:
- The encrypted packet traffic.
- The decryption function to actually decrypt and inspect or forward the decrypted results to the tools that will inspect and monitor.
- The final, symmetric encryption keys used to encrypt and decrypt those packets.
Number 1, getting the packet traffic is easy. Inline devices are likely placed at strategic control points in your network giving you access to your network traffic. Out-of-band solutions such as TAPs, mirrors and packet brokers have been capturing and brokering traffic for inspection for years. Even new environments like the public cloud are building in infrastructure-level mirroring capabilities.
Number 2, doing the actual decryption, is easy. Decrypt functions have been built into hardware and software libraries for years. If you have the ingredients - the packets and the keys, decryption is a straightforward mathematics operation for which chips, firmware and software have been optimized.
It’s number 3, getting the final symmetric encryption keys, that is the challenge. In fact, all of modern decrypted visibility comes down to this fundamental key challenge. These are not the public/private key pairs or pre-shared secrets. These are the ephemeral keys that are derived, independently, for each session by the TLS client and the TLS server. These are the keys that actually do the encryption / decryption. Modern TLS standards have made regenerating these keys impossible. Modern ciphers like Diffie-Hellman and any PFS enabled system have made terminating and proxying TLS sessions in order to have access to the final symmetric keys expensive and, in a growing number of use cases, prohibitively and architecturally expensive.
This is the key challenge faced by all current and legacy methods of doing decryption. PFS killed the ability to use pre-configured public/private keys. TLS 1.3 encrypts certificate exchange, killing out-of-band handshake replay ability. Certificate pinning kills MITM. Yet in each of these cases, the encrypted packet traffic can be decrypted if the symmetric keys are known.
A New Approach
Our approach at Nubeva re-examines how to solve the problems of legacy decryption methods. In a TLS session, a handshake occurs to authenticate and begin the key exchange process, which enables secure communications between client and server. In the handshake, the server uses its public/private key pair to arrive at a symmetric key. Sometimes referred to as the master secret, the shared secret, the ephemeral key, and more. This key is not the TLS server public or private key but the actual cipher key, shared by both the TLS client and server, to perform the actual bi-direction (symmetric) encryption and decryption of traffic. This symmetric key is unique per session and temporary. It enable high speed, efficient, commodity encode encryption/decryption for the conversation. This symmetric key is enabling high-speed communication. The symmetric key is required to both encrypt and decrypt traffic for the duration of the session and then is discarded. And, at the most fundamental level, it’s this key that is needed to decrypt traffic if one is to inspect or monitor it - no matter the application of inline or passive.
As noted above, the legacy methods use very complicated methods to get to this key in order to perform simple decryption. They are complicated, expensive, heavy and have not been updated in two decades. So, it’s time to re-think how to see and monitor this traffic. Read on to learn how Nubeva’s solution discovers, captures and uses symmetric keys to decrypt and see all network traffic.
What is Symmetric Key Intercept?
Nubeva Symmetric Key Intercept allows enterprises to discover the final symmetric session keys from TLS clients and/or servers in real time and delivers these keys to decryption engines of choice. This process lets DevOps and security teams see more traffic while enhancing performance. It’s easy to deploy and improves existing functionality of security and monitoring tools already in place.
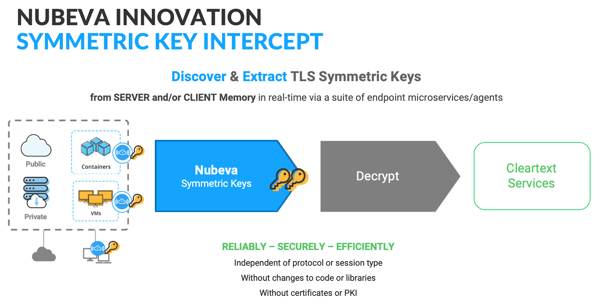 Symmetric Key Intercept introduces a new methodology for decrypting TLS session data. Since the symmetric keys already exist in active memory while the session is active, Nubeva’s microservices technology discovers, extracts and reuses the session specific keys, skipping the complicated and costly processes of the past. Because Nubeva discovers the final session keys out of memory, it works independent of protocol or cipher suite, requires no changes to code or libraries on the host and does not require certificate or server key management.
Symmetric Key Intercept introduces a new methodology for decrypting TLS session data. Since the symmetric keys already exist in active memory while the session is active, Nubeva’s microservices technology discovers, extracts and reuses the session specific keys, skipping the complicated and costly processes of the past. Because Nubeva discovers the final session keys out of memory, it works independent of protocol or cipher suite, requires no changes to code or libraries on the host and does not require certificate or server key management.
Nubeva allows you to extract the keys and forward them securely over a TLS encrypted session over a secure network to decryption systems. The process is so efficient that you can extract and export keys in less than 100 microseconds after the handshake and deliver the keys 20 milliseconds before the first encrypted packet arrives from any packet delivery service, such as a NPB, tap, spans, or mirrors. Once the keys are there, the traffic can be decrypted for inspection.
The benefits of this approach include:
- Seeing more traffic - Nubeva can get keys from traffic 98% of the time, from either the client or server side and ours is the only system that handles 3rd party sessions, pinned applications and works regardless of protocol or ciphers.
- Boosting performance - The ability to skip the handshake replay and employ bulk decryption methods allows you to significantly reduce the decryption steps and improve throughput while reducing latency and interruptions. As a result, this reduces the cost of decrypted visibility.
- Simplicity - The “fire and forget” architecture requires no certificate management and creates one common solution across all applications and implementations.
For more on how Symmetric Key Intercept works, how it scales and security of the method, watch the Technical Brown Bag.
The Last Word: Use Cases
- Enhance and boost inline systems: Symmetric Key Intercept let’s you see into your network traffic at line rate speed (no latency with full packet inspection). End users can deploy Symmetric Key Intercept decrypts traffic for inspection with ease using existing commercial or open source tools. Manufacturers can build Symmetric Key Intercept into their systems to feed the keys directly into these systems for decryption.
- Restore and expand passive systems. If you have dedicated monitoring systems or visibility appliances, they’re going blind to PFS traffic embodied in TLS 1.2 and 1.3. This means you can’t see traffic to your cloud platforms, service providers and to the internet. Symmetric Key Intercept restores visibility to this traffic by deploying sensors and sending keys directly to the decryptor (skipping expensive certificate management and key regeneration). It provides access to pure symmetric decryption enabling you to see all PFS and 3rd party traffic and eliminates the certificate and key management complexities embedded in these systems.
- Create and enable greenfield visibility. Where decrypted visibility was never before possible, Symmetric Key Intercept enables users to inspect intra-zone/VPC traffic, container and Kubernetes environments, cloud and 3rd party API calls, pinned traffic and more. Now you can run high-speed, out-of-band decryption on commodity hardware and achieve output rates never before possible.
For more about Symmetric Key Intercept, connect with us at info@nubeva.com. We can provide you with a quick demo, answer questions and help you get set up for a free 30-day trial.

